- Print
- DarkLight
- PDF
Security and data governance
This document contains technical information for IT security managers and DPOs.
Summary
Cooperlink's general policy is to retain as little data as possible to provide the service and to preserve the autonomy and ownership of each company's data. Cooperlink therefore puts the security of business data and private data at the center of its concerns. In particular, the following measures are applied (not exhaustive):
- Data segregation through by-design / by-default integration
- High degree of security for access to data by users and partners
- Compliance with best practices for development and deployment (OWASP, Firewall, Reverse Proxy, ...)
- Logical and/or physical isolation of customer installations
- Strict organisational measures (e.g. access to limited production sites, asset encryption, NDA, etc.)
- Implementation of the principles of privacy-by-design and privacy-by-default
- Monitoring, backups and event logging (audit trail)
- Business Continuity and Disaster Recovery Plans
- Distributed/hybrid architecture
- Adherence to the requirements of the ISO27001 standard
For more detailed information, please read the rest of this article.
Detailed version
Governance
Cooperlink's general policy is to retain as little data as possible to provide the service and to preserve the autonomy and ownership of each company's data. Cooperlink's development team follows best practices in its development. In particular, it follows the OWASP guideline for protection against cyber-attacks. Authentication and connectivity to the database go through generally accepted technologies: Spring security, JWT tokens, Hibernate, ... | Minimum Data Retention Policy Adherence to development best practices |
Data security
The connection of the company's employees to third-party systems through Cooperlink is carried out by identity delegation, which guarantees the preservation of access rights and data security. This means that the user obtains the same rights to access the company's tools directly as to access them via Cooperlink. Authentication is carried out through modern protocols (e.g. OAuth) when the third-party system supports it. The connection of the partners is protected by Cooperlink which acts as a proxy. Under no circumstances do partners have direct access to the company's tools. The documents exchanged within the workspace are hosted in a separate and isolated storage space (shadow storage). Access to documents in workspaces is made from this storage space through the bridge service(message broker). They therefore ensure the security and segregation of data. Cooperlink servers are protected by firewall and reverse proxy. All data in transit is end-to-end encrypted in SHA-256/TLS, and a chunking method is applied on the bridge service. All communications require an HTTPS connection. All data from all customers and partners is logically (or physically in the case of remote communications) separated and linked to a unique corporate identifier. | Connection of (internal) users to third-party systems by identity delegation. Isolated and secure partner access through shadow storage and message broker. All connections are protected by firewall and reverse proxy. All data in transit is end-to-end encrypted. Customer and partner data is logically or physically isolated. |
Application Security
A decoupling is carried out between the storage and processing of the data. The database that operates Cooperlink is isolated from the application. Each user has a personal account on Cooperlink, as well as delegated access to the company's tools (see above). Application administrators can assign roles to users with a custom set of permissions. All user activities, API, automated processes, etc. are recorded in an audit trail log. In the event of a critical security breach, Cooperlink implements the necessary means as quickly as possible in accordance with its terms and conditions. | Principle of native data segregation via integration-by-default / integration-by-design. Rights and permissions. Audit trail. |
Protection of private data
Cooperlink adheres to the GDPR regulation and shall be considered by the customer as a data processor when it provides hosting, outsourcing and/or has access to the data (e.g. for configuration) . In this case, a private data processing agreement must be signed between the parties (DPA - Data Processing Agreement). The customer is in any case considered as a Data Controller. Cooperlink provides a high level of security, suitable for normal use of services, namely the management of construction projects in a professional context. The customer and users agree to use the platform for this purpose. In general, it is recalled that Cooperlink provides the means to securely exchange information between companies (including documents, and emails if necessary). It is the Responsibility of the Data Controller to verify that the sensitivity of this information (as well as the content of documents and emails) complies with the security measures put in place by Cooperlink. Cooperlink has no control over the use of the platform by the Data Controller, it can not be held responsible for the data and content exchanged. Cooperlink has been developed taking into account the principles of privacy-by-design and privacy-by-default. The processing of the data is necessary for the performance of the contract between the Data Controller and its partners, or failing that, for the pursuit of legitimate interests (guaranteeing the security of information and processing information relating to commercial projects in particular). It is limited to the data necessary for the proper performance of the service. The nature and purpose of the processing of the personal data of the controller are
The Data Controller is solely responsible for all data inserted in Cooperlink (for example, a comment, the description of a task, the title of a document, its content, a note, ...). Cooperlink only communicates personal data to third-party services for
With the exception of these services, personal data is processed exclusively by Cooperlink and, where applicable, by the management team and by trusted senior managers who have received prior training. | Cooperlink adheres to the GDPR regulation. Cooperlink provides a high level of security, suitable for normal use of services, namely the management of construction projects in a professional context. Cooperlink has been developed taking into account the principles of privacy-by-design and privacy-by-default. |
Audit trail
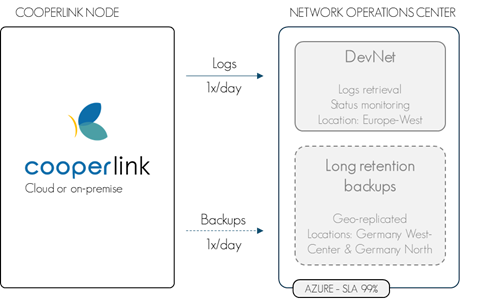
Cooperlink records all business activities, application events and a list of errors. Nearly 150 events are listed including editing a file, renaming, publishing to a partner, downloading, uploading, adding users, changes in rights, ... The most important information is disseminated in the application and/or in the API. Cooperlink logs are archived twice a day for long-term archiving in a space accessible only to administrators. Cooperlink also logs application activities (connection attempts, etc.). | Cooperlink records events as an archived log twice a day. |
Backup copies
A backup copy of the database is made daily. For cloud customers, this copy is kept in Cooperlink's cloud infrastructure. For on-premise clients, this copy is stored on a network server. The customer can subscribe to a long-retention backup copy on a dedicated server. | Cooperlink has a daily backup policy. |
Security Controls
Cooperlink's access to production sites for installation and maintenance requires a VPN or SSH, and IP restriction based on fixed IP addresses. Access to these nodes is only performed by management and trusted staff who have received prior training. Cooperlink has a strict internal policy on the protection of data, and more specifically personal data, within the company, including:
| Implementation of strict organizational measures (e.g. access to limited production sites, asset encryption, NDA, ...) |
Evolutions of the application
Cooperlink has separate environments for development, testing and production. The technical team follows an agile development method based on sprints lasting approximately 1 month followed by a quality control procedure. Before a new version is put into production, a code review is carried out by Cooperlink executives or trusted employees with more than 15 years of experience in application development. | Agile development method with supervision by qualified personnel. |
Monitoring and alert procedures
Cooperlink has developed a Network Operations Center that is an integral part of its overall Information Security Management System (ISMS). This center continuously evaluates the availability of service at Customers, load parameters and collects error reports for regular monitoring and fast processing. Cooperlink also provides a user portal to report at https://support.cooperlink.io > Report incident or data breach. Cooperlink maintains a record of incidents detected in production environments as well as a record of user reports. The processor monitors the application's analytical data and regularly evaluates its usage. Inconsistent use or abnormal application load is reported internally and handled promptly. Logs and alerts are evaluated daily by the management team and by trusted senior managers who have received pre-training.
| Continuous monitoring of the Cooperlink network and existence of procedures in the event of an incident or potential data leak. |
Business Continuity and Disaster Recovery Plans
Through its (distributed) network architecture and integration with third-party systems, Cooperlink offers a high degree of reliability to ensure business continuity. This is because an incident that appears on a dedicated environment does not affect the availability of the service in other environments. In the event of a major failure of Cooperlink resulting in the interruption of the exchange service and automated data processing, the information stored on third-party systems remains fully accessible. This architecture therefore provides users with continuity of their critical activities. Apart from these elements, Cooperlink has implemented the following strategy to ensure the continuity of services including:
| High degree of reliability through integration with third-party systems. Business continuity and disaster recovery plans. |
Software architectures and deployment
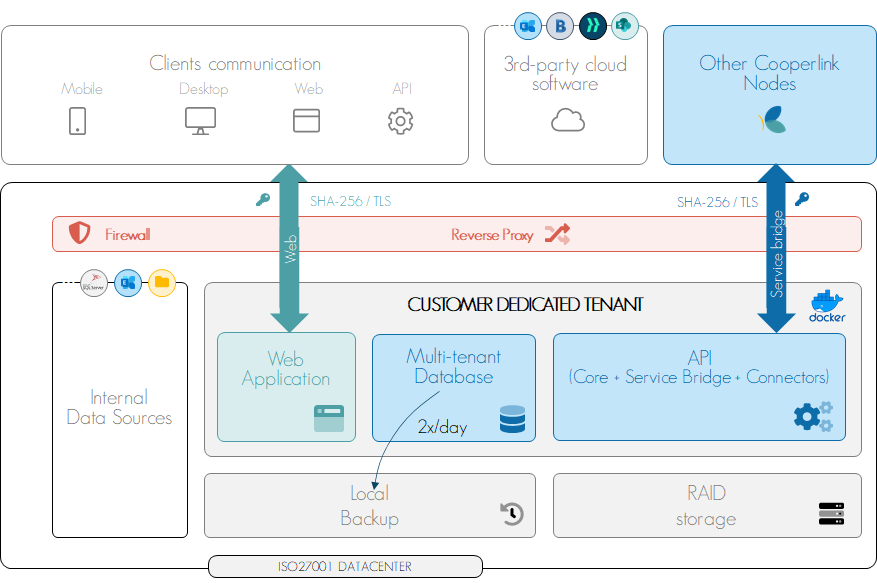
Cooperlink's software architecture is service-oriented (SOA), multi-tenant, including a communication bus (message broker called Service Bridge) between local and/or public tenants. Unless explicitly required by the Customer, the files are not stored by Cooperlink. Cooperlink offers a hybrid deployment architecture, whose node installation type is at the Customer's choice: public cloud, dedicated cloud or on-premise. In this way, the Customer has full control over the location of his data.
Example of deployment architecture | Distributed/hybrid software architecture. The customer chooses between public cloud, dedicated cloud or on-premise. Storage in an ISO27001 environment available upon request. |
Adherence to ISO27001 standard
Cooperlink intends to comply with the ISO27001 standard and is currently taking steps to be ISO27001 certified quickly. To do this, Cooperlink is currently taking the following actions:
While awaiting ISO27001 certification, Cooperlink details and proves the security measures implemented and offers its customers all the necessary transparency in this regard. | Cooperlink adheres to the ISO27701 standard |